 |
|||||||||
|
|||||||||
tcACCESS
tcACCESS – Features
Data Mapping and Intelligent Import Functions for any file structures To avoid the manual definition of Mainframe file structures, tcACCESS can automatically import data structures defined in source programs or in copybooks. All relevant data formats are automatically recognized (packed, zoned, hexadecimal, alphanumeric, binary etc.). Redefined data structures are also supported. 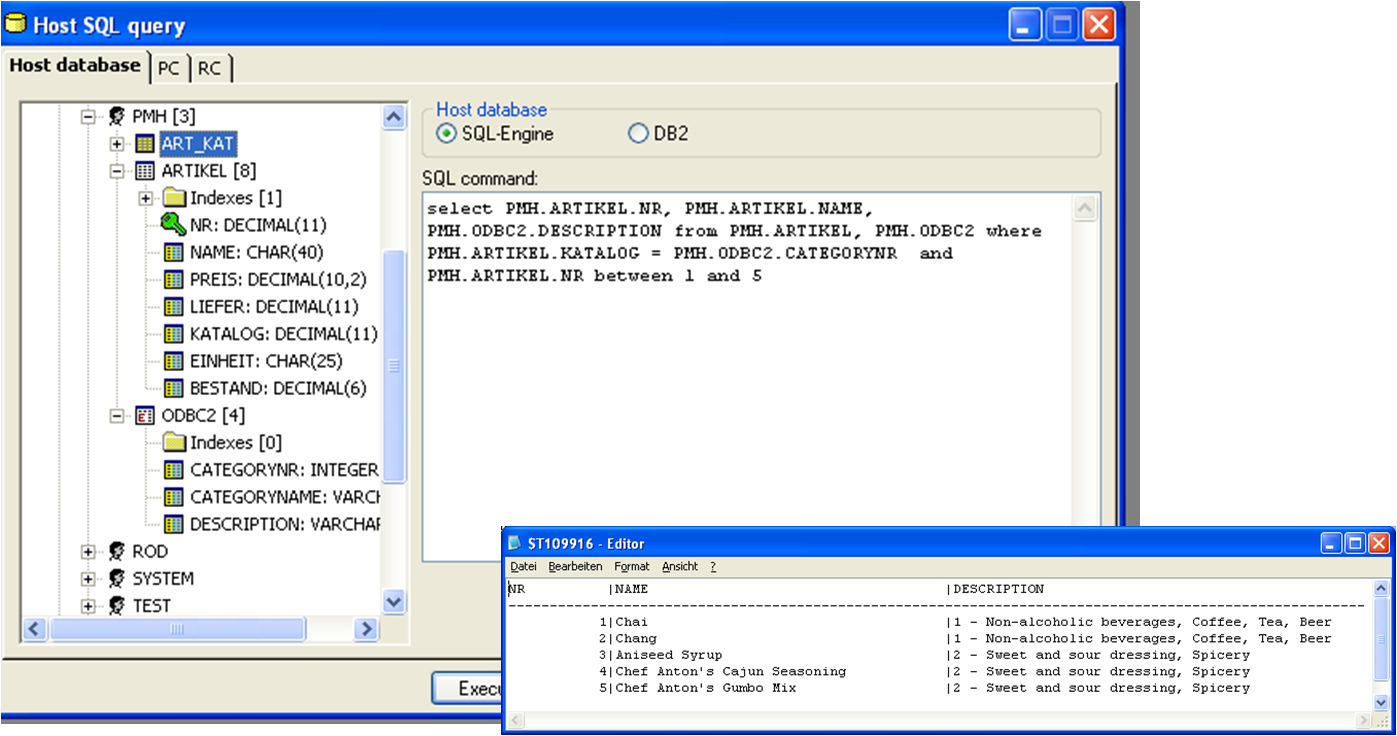 Data Mapping and Intelligent Import Functions for databases Segment data structures for DL/I and IMS/DB are automatically imported like any other file formats. Specific information for accessing the database (SSA information) is automatically retrieved from DBD and PSB modules. This information is important, because tcACCESS bases the access strategies on this information. Especially for decisions to perform a keyed or a sequential access. For ADABAS and CA-Datacom/DB, the corresponding data dictionary system will be used (i.e. PREDICT). Database specific information is automatically recognized (Index information, Descriptor and Super Descriptor Information, Periodic Group Fields, Multiple Fields etc.). The resulting tcACCESS field definitions are presented to the administrator and changes may be applied if needed. SCHEMA data will be evaluated for CA-IDMS. All information necessary to establish the proper relationships are automatically extracted.
Process Management All tcACCESS server components available for MS Windows, UNIX/LINUX/Linux on System z and JAVA contain Mainframe-applications can directly initiate processes and applications on Windows- or UNIX/LINUX/Linux on System z systems and can pass parameter and data to them. The processes on the Open Server platforms that have been initiated pass back return codes or return messages to the mainframe program. This guarantees a two way communication and a secure process management. Databases on different platforms can be kept in synch. Applications that change mainframe data can pass the changes to Open Server applications using the tcACCESS process management and Listener functions. Features :
tcACCESS administrative functions and Batch processors An MS-Windows application is provided to configure, control, monitor and analyze tcACCESS operations. This application also displays all mainframe data sources in a tree structure. All field and index information will be shown. Depending on the user sign on, security rules are applied so that the user is only able to access data sources that are part of his security profile (i.e. RACF). Based on the information provided by tcACCESS, the user can easily select data from mainframe data sources and transfer them to another system without any detailed knowledge about the mainframe. All the advantages of the SQL- Engine apply. tcACCESS will automatically optimize the access to the data source. Key fields, alternate indexes, Descriptors and Super-Descriptors will be taken into account to achieve maximum path optimization and optimum system performance. Scheduling functions for bi-directional data transfer tcACCESS can transfer data in both directions between the IBM mainframe and another system. This data transfer can be completely automated and initiated from either side. The data transfer can be scheduled to start at a specific time or on a specific event. Interfaces are available to integrate tcACCESS into existing scheduling procedures. Structured data transfer In a tcACCESS environment there is no need to transfer entire files from the mainframe to a workstation and then select the records on the PC for further processing. tcACCESS knows the data format and the data structure, it can select the data from the mainframe data sources based on logical conditions and creates a physical record which only contains the desired fields that will be downloaded to the PC. These data portions also meet security requirements. Another aspect is performance; the data transfer rate can be increased because the amount of transferred information is reduced. Networking bandwidth can be saved. Compression To reduce the amount of data transmitted and to provide optimum response times, tcACCESS provides a compression algorithm. Data will be compressed before it is transmitted and decompressed when it is received. Depending on the file structure, compression rates up to 90% can be achieved. Using this compression algorithm, resources needed for the data transfer can be reduced to the absolute minimum. Controlling functions For all LU2 based data transmissions, tcACCESS performs a 32 Bit CRC (Cyclic Redundancy Check) checksum test. This test guarantees data integrity. tcACCESS provides logging and monitoring functions that create audit trails for every communication request. The log data can also be used for charge back procedures. The data transmission procedures can be automated and integrated into IT process flows. Every tcACCESS process terminates with a return code, indicating the success or failure of the process, hence automatic actions can be performed. Monitoring tcACCESS provides a facility to monitor all data exchange operations. The tcACCESS Request Monitor makes the administration easier and the data exchange becomes more transparent. Due to the rich functionality of tcACCESS, it is possible to implement data integration solutions in a short period of time, even without any programming. Features
Security tcACCESS supports the SAF interface. This provides simple integration into well-known Mainframe Security Systems like RACF, TOP SECRET or ACF2. This integration ensures that a PC or WEB user can only work with those host files for which he has the necessary authorization. The security rules defined in the security systems fully apply to Web- applications that directly access mainframe data sources (read/write/update). tcACCESS also offers a security concept that can be used instead or in combination with the SAF interface. If the organization is using an in-house developed security system, tcACCESS will also support this. Features:
tcACCESS Virtual Disk All administrative information is stored by tcACCESS on a mainframe disk. This disk, however, is organized in such a way that it can be simultaneously accessed and maintained by authorized workstation users as well as host- programs. The "Virtual Disk" introduces a new data source that can be accessed by different systems. It can be used as a central backup repository or act as a resource for information distribution. It may even be possible to replace decentralized server implementations by using the Virtual Disk architecture. The Mainframe can act as a data server in various ways. Private networks, which are connected to a mainframe but not to each other, can now exchange data using the "Virtual Disk". Access to the "Virtual Disk" is transparent because it is integrated into MS Windows Explorer. The user can simply drag and drop files from the Virtual Disk or onto the Virtual Disk. Features:
© 2022 aMod. All Rigths Reserved. |